Nabu Casa Is A Security Risk For Your Home Assistant Installation
The is a serious security downside to using Nabu Casa and there is a strong argument to be made that it does not outweigh the benefits. This post explores these weak security protections.
The is a serious security downside to using Nabu Casa and there is a strong argument to be made that it does not outweigh the benefits. What's more, Nabu Casa charges you for a service that is exposing your Home Assistant installation to the world and does not offer the protections of modern authentication.
The security risk
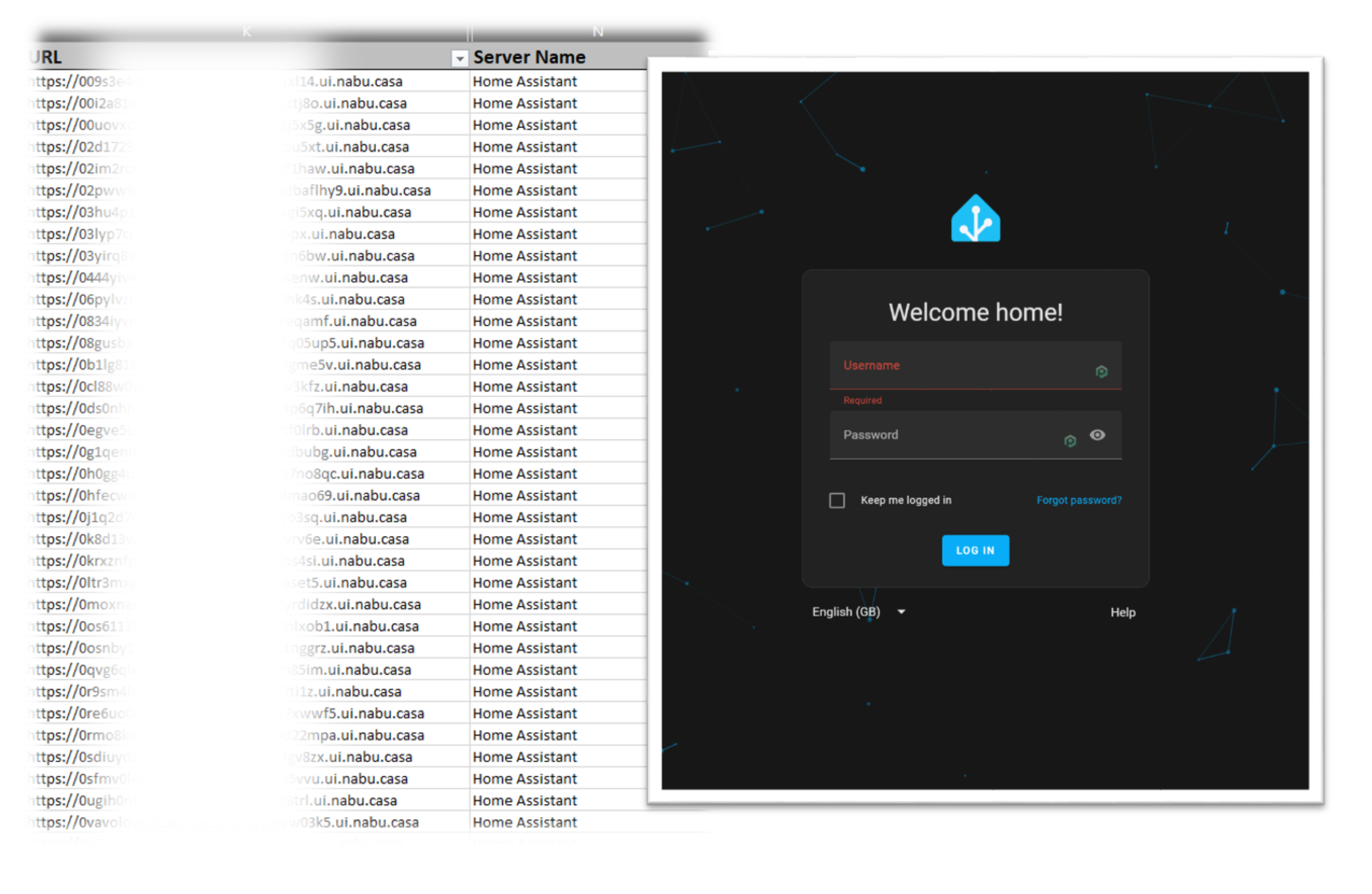
Nabu Casa is a cloud service that allows you to access your Home Assistant installation from anywhere. This is a great feature, but it also means that your Home Assistant installation is exposed to the world via their proxy service. When you sign up for Nabu Casa, you are given a uniqueURL that is used to access your Home Assistant installation - these URLs at face value are random and obscure, but unfortunately this does not protect your Home Assistant installation from DNS enumeration.
Home Assistant is a service that a lot of people entrust with more than just smart bulbs and robot vacuum cleaners. Let's explore what DNS enumeration looks like and how many Nabu Casa connected instances we can discover with some publicly available penetration testing tools.
Project Discovery - SubFinder
https://github.com/projectdiscovery/subfinder
Here is the command that found over 5900 public facing Home Assistant instances in under 5 minutes:
subfinder -d ui.nabu.casa -o subdomains.txt -r 1.1.1.1
A DNS record on its own does not prove that a host is alive. So let's spend another 5 minutes and validate which hosts are live with another great Project Discovery tool, HTTPX:
httpx -l subdomains.txt -status-code -title -tech-detect -server -csv -o results.csv
And there you have it in ten minutes, we have enumerated 5905 active Home Assistant instances that are presenting their login page. Sadly ths most likely only scratches the surface of what is out there. Tool such as Murklemap, running DNS enumeration and search tools claim to have upwards of 607,000 valid subdomains for ui.nabu.casa: https://www.merklemap.com/search?query=*ui.nabu.casa.
Let's hope they all have complex passwords and Multi-Factor Authentication enabled: https://www.home-assistant.io/docs/authentication/multi-factor-auth/.
Unlike alternative remote‑access solutions that enforce an external authentication layer (e.g., OAuth/SSO), the Nabu Casa proxy does not provide additional access control beyond TLS termination. As a result, the Home Assistant login page and associated authentication endpoints are directly reachable by unauthenticated users.
In addition to the Home Assistant login page is publicly accessible via a Nabu Casa URL, the proxy service forwards all authentication‑related endpoints (/auth/*, WebSocket API handshake, REST API) directly to the Home Assistant instance.
This configuration does not constitute a vulnerability on its own; however, it increases the potential impact of any future Home Assistant authentication flaw.
Weak Security At A Cost
The worst part of this Nabu Casa service is that you are paying a fee to expose your instance without modern auth.
Previous communications from Nabu Casa developers suggest that the Home Assistant project was aimed at home users would see no value in using SSO:
Home Assistant is aimed at a Home user, the home environment. IMHO this proposal/open letter is for feeding the enterprise smart home syndrome. I am pretty sure my dad (or any other average user of Home Assistant) isn’t using SSO to log in to his home devices.
Nabu Casa offer fair pricing for the service and as well as the proxying service, it allows you to easily setup Google Assistant and Amazon Alexa in control your Home Assistant instance. Furthermore this goes towards supporting what is otherwise a brilliant free and open source project. The community has a lot to thank the Nabu Casa and Open Home Foundation for, but security is more important than ever.
As previously mentioned Home Assistant has become much more than a way to see the temperature in your bedroom, people are using it in combination with smart locks, alarm systems, CCTV and presence detection. Enterprising criminals and organised crime are potentially being handed everything they need to walk into your property without challenge or detection. We cannot emphasise this enough, public exposure of Home Assistant, fronted with poor authentication could lead to a serious compromise or your Home's safety and security.
A Secure Nabu Casa Alternative
homeway.io
Homeway.io gives you remote Home Assistant access without exposing a public login page. It sits in front of HA with Google/Apple sign-in as the first gate, so you inherit their MFA and risk controls before anyone can even reach your HA auth flow. Traffic rides an outbound WebSocket tunnel (no open ports, no DNS enumeration surface), and you still keep the convenience of Google Assistant and Alexa integrations.
This project seems to have spawned out of frustration with the Home Assistant Developers and is even more fairly priced; including a free tier of the service.
We suggest this the strong caveat that homeway.io and services like it are only as secure at the account you configure it with. Weak passwords and no malicious login lockouts or detection could still lead to a account and Home Assistant takeover.
Tailscale
Don't want to expose your Home Assistant instance at all? Tailscale might be the private VPN service that you are looking for.
Tailscale gives you remote Home Assistant access without exposing it to the internet. Instead of publishing your login page through a public reverse proxy, Tailscale builds a private, peer‑to‑peer mesh over WireGuard that only your authenticated devices can reach. You get end‑to‑end encryption, device‑level MFA, and zero open ports—no DNS enumeration, no credential stuffing against a public endpoint, and no extra auth layer to bolt on. It behaves like you’re on the same LAN from anywhere, while staying invisible to everyone else.
Tailscale is a maturing project and has documentation and use case examples over at their blog: https://tailscale.com/blog/how-tailscale-works.
DataSolace Closing Note
We built our careers on security research and secure devops practices. If you’re looking for support from whether that’s home automation advice, a security overview, or help implementing best‑practice controls, we’d be happy to talk. Get in touch and we can discuss how we can help automate what you do, securely.
